CYBERSECURITY FOR CRITICAL INFRASTRUCTURES
Are you an operator of critical infrastructure , and do you need to keep a close eye on the integrity of your data? According to Bitkom Research, 84% of companies surveyed in the critical infrastructure sectors expect an increase in cyberattacks in the next 12 months.
The requirements for critical infrastructure operators are increasing accordingly. Section 2 “Energy” of the BSI-KRITIS-Regulation, for example, mandates the establishment and certification of an information security management system. ISO 27001 27001 contains protection goals and states that cryptography and firewalls should be used. In addition, IEC 62443 specifies the requirements for controlling physical systems. Section 8 “Transport and Traffic” regulates the requirements for public transport, trans-European network corridors and the IP network related to rail operation.
With the successful market launch of our new product cryptOHBguard® into the product range of the cyberOHBguard series, we can cover all of the aforementioned matters and requirements. This enables widely networked, secure digitalisation projects to be implemented under demanding environmental conditions.
Wherever you need a large number of decentralised cybersecurity components to be deployed in a “harsh” environment, cyberOHBguard series products are the preferred choice. In addition to their application in rail networks, our solutions are also suitable for the following industries and fields of application:
- Digitalisation of energy transfer or transport networks::
Secure data connections as a basis for the smart control of complex network infrastructures and more efficient load and feed-in management. - Digitalisation of motorway/transportation infrastructure::
Secure data encryption and transmission for autonomous driving and intelligent traffic routing with minimal latency, even under extreme temperature conditions - Digitalisation of waterway infrastructure:
Solutions for automated and networked inland waterway transport as a basis for increased utilisation of waterways and as a result environment-friendly goods transport
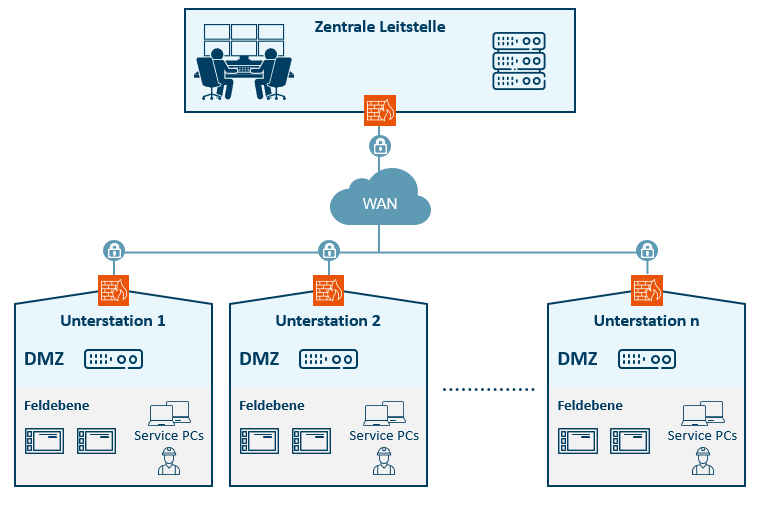
DMZ as protection against unauthorized access to security-relevant systems
A demilitarized zone (DMZ) is a computer network with security-controlled access to the servers connected to it.
The systems in the DMZ are shielded from other networks by firewalls. This separation allows access to publicly accessible services and at the same time protects the internal network from unauthorized access from outside. The purpose is to make services of the computer network available to both the WAN and the LAN on a secure basis.
A DMZ provides protection by isolating a system from two or more networks.
Our DMZ solution consists of a firewall and an industrial PC as the hardware basis, on which all applications relevant to the application are implemented as virtual machines.
With our cyberOHBguard series, widely networked, secure digitalisation projects can be implemented under demanding environmental conditions.
With our new cryptOHBguard® system, we ensure encrypted communication between the field equipment and the control centres via the IEC 60870-5-104 protocol, secured by genuscreen firewall. Both the hardware and the firewall are BSI-certified, which significantly increases basic protection.
The cryptOHBguard® 10scs is your preferred option for application at field level in a “harsh” environment.
For application in the decentralised data centre environment, we recommend the cryptOHBguard® S-XXL.
With the manageOHBguard®, more than 10,000 components can be managed centrally in one tool. This is used to detect anomalies in the system. If required, parts of the network or individual components can be deactivated automatically.
With the manageOHBguard®, more than 10,000 components can be managed centrally in one tool. This is used to detect anomalies in the system. If required, parts of the network or individual components can be deactivated automatically.
To ensure the full traceability of all components, these are labelled with a unique GS-1 QR code. This provides tamper protection and ensures that an attack on any key material contained in the equipment can be detected from production right up to implementation at the customer.